javax.net.ssl.SSLException:收到致命警报:protocol_version
之前有没有人遇到此错误?我是SSL的新手,我的ClientHello有什么明显的错误吗?抛出该异常时没有ServerHello响应。任何建议都表示赞赏。
*** ClientHello, TLSv1
RandomCookie: GMT: 1351745496 bytes = { 154, 151, 225, 128, 127, 137, 198, 245, 160, 35, 124, 13, 135, 120, 33, 240, 82, 223, 56, 25, 207, 231, 231, 124, 103, 205, 66, 218 }
Session ID: {}
Cipher Suites: [SSL_RSA_WITH_RC4_128_MD5, SSL_RSA_WITH_RC4_128_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_DES_CBC_SHA, SSL_DHE_RSA_WITH_DES_CBC_SHA, SSL_DHE_DSS_WITH_DES_CBC_SHA, SSL_RSA_EXPORT_WITH_RC4_40_MD5, SSL_RSA_EXPORT_WITH_DES40_CBC_SHA, SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA, SSL_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
***
[write] MD5 and SHA1 hashes: len = 75
0000: 01 00 00 47 03 01 51 92 00 D8 9A 97 E1 80 7F 89 ...G..Q.........
0010: C6 F5 A0 23 7C 0D 87 78 21 F0 52 DF 38 19 CF E7 ...#...x!.R.8...
0020: E7 7C 67 CD 42 DA 00 00 20 00 04 00 05 00 2F 00 ..g.B... ...../.
0030: 33 00 32 00 0A 00 16 00 13 00 09 00 15 00 12 00 3.2.............
0040: 03 00 08 00 14 00 11 00 FF 01 00 ...........
xxx, WRITE: TLSv1 Handshake, length = 75
[write] MD5 and SHA1 hashes: len = 101
0000: 01 03 01 00 3C 00 00 00 20 00 00 04 01 00 80 00 ....<... .......
0010: 00 05 00 00 2F 00 00 33 00 00 32 00 00 0A 07 00 ..../..3..2.....
0020: C0 00 00 16 00 00 13 00 00 09 06 00 40 00 00 15 ............@...
0030: 00 00 12 00 00 03 02 00 80 00 00 08 00 00 14 00 ................
0040: 00 11 00 00 FF 51 92 00 D8 9A 97 E1 80 7F 89 C6 .....Q..........
0050: F5 A0 23 7C 0D 87 78 21 F0 52 DF 38 19 CF E7 E7 ..#...x!.R.8....
0060: 7C 67 CD 42 DA .g.B.
xxx, WRITE: SSLv2 client hello message, length = 101
[Raw write]: length = 103
0000: 80 65 01 03 01 00 3C 00 00 00 20 00 00 04 01 00 .e....<... .....
0010: 80 00 00 05 00 00 2F 00 00 33 00 00 32 00 00 0A ....../..3..2...
0020: 07 00 C0 00 00 16 00 00 13 00 00 09 06 00 40 00 ..............@.
0030: 00 15 00 00 12 00 00 03 02 00 80 00 00 08 00 00 ................
0040: 14 00 00 11 00 00 FF 51 92 00 D8 9A 97 E1 80 7F .......Q........
0050: 89 C6 F5 A0 23 7C 0D 87 78 21 F0 52 DF 38 19 CF ....#...x!.R.8..
0060: E7 E7 7C 67 CD 42 DA ...g.B.
[Raw read]: length = 5
0000: 15 03 01 00 02 .....
[Raw read]: length = 2
0000: 02 46 .F
{http://xml.apache.org/axis/}堆栈跟踪:
javax.net.ssl.SSLException: Received fatal alert: protocol_version
at com.sun.net.ssl.internal.ssl.Alerts.getSSLException(Alerts.java:190)
at com.sun.net.ssl.internal.ssl.Alerts.getSSLException(Alerts.java:136)
at com.sun.net.ssl.internal.ssl.SSLSocketImpl.recvAlert(SSLSocketImpl.java:1806)
at com.sun.net.ssl.internal.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:986)
at com.sun.net.ssl.internal.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1170)
at com.sun.net.ssl.internal.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1197)
at com.sun.net.ssl.internal.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1181)
at org.apache.axis.components.net.JSSESocketFactory.create(JSSESocketFactory.java:186)
at
...
15 个答案:
答案 0 :(得分:27)
在Java 1.8上,默认TLS协议是v1.2。在Java 1.6和1.7上,默认是已废弃的TLS1.0。我在Java 1.8上遇到此错误,因为url使用旧的TLS1.0(就像你 - 你看到ClientHello, TLSv1)。解决此错误您需要使用Java 1.8的覆盖默认值。
System.setProperty("https.protocols", "TLSv1");
有关Oracle blog的更多信息。
答案 1 :(得分:9)
marioosh's answer seems to on the right track. It didn't work for me. So I found:
Problems connecting via HTTPS/SSL through own Java client
which uses:
java.lang.System.setProperty("https.protocols", "TLSv1,TLSv1.1,TLSv1.2");
Which seems to be necessary with Java 7 and a TLSv1.2 site.
I checked the site with:
openssl s_client -connect www.st.nmfs.noaa.gov:443
using
openssl version
OpenSSL 1.0.2l 25 May 2017
and got the result:
...
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
...
Please note that and older openssl version on my mac did not work and I had to use the macports one.
答案 2 :(得分:5)
在尝试安装PySpark软件包时遇到了此问题。我通过使用环境变量更改TLS版本来解决此问题:
echo 'export JAVA_TOOL_OPTIONS="-Dhttps.protocols=TLSv1.2"' >> ~/.bashrc
source ~/.bashrc
答案 3 :(得分:4)
这似乎是协议版本不匹配,当客户端使用的SSL协议版本与服务器不匹配时,通常会发生此异常。您的客户应使用服务器支持的proctocol版本。
答案 4 :(得分:3)
@marioosh添加了一些关于密码套件加密的额外信息。
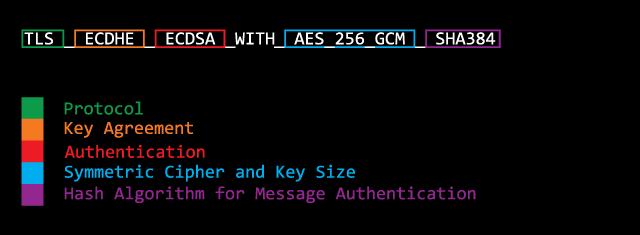
cipher suite是主机用于在传输层安全性(TLS)/安全套接字层(SSL)网络协议中建立安全通信的对称和非对称加密算法的集合。
密码是算法,更具体地说,它们是执行加密和相应解密的一系列步骤。
密码套件为以下每项任务指定一种算法:
- 密钥交换
- 批量加密
- 消息身份验证
SocketFactory «默认握手协议«为避免SSLException,请使用https.protocols系统属性。
它包含以逗号分隔的协议套件名称列表,用于指定在此HttpsURLConnection上启用的协议套件。请参阅SSLSocket.setEnabledProtocols(String[]) method。
System.setProperty("https.protocols", "SSLv3");
// (OR)
System.setProperty("https.protocols", "TLSv1");
JAVA8«TLS 1.1和TLS 1.2默认启用:默认情况下,SunJSSE提供程序在客户端上启用协议TLS 1.1和TLS 1.2。
System.setProperty("https.protocols", "TLSv1,TLSv1.1,TLSv1.2");
Java8网络文件示例:
public class SecureSocket {
static {
// System.setProperty("javax.net.debug", "all");
System.setProperty("https.protocols", "TLSv1,TLSv1.1,TLSv1.2");
}
public static void main(String[] args) {
String GhitHubSSLFile = "https://raw.githubusercontent.com/Yash-777/SeleniumWebDrivers/master/pom.xml";
try {
String str = readCloudFileAsString(GhitHubSSLFile);
// new String(Files.readAllBytes(Paths.get( "D:/Sample.file" )));
System.out.println("Cloud File Data : "+ str);
} catch (IOException e) {
e.printStackTrace();
}
}
public static String readCloudFileAsString( String urlStr ) throws java.io.IOException {
if( urlStr != null && urlStr != "" ) {
java.io.InputStream s = null;
String content = null;
try {
URL url = new URL( urlStr );
s = (java.io.InputStream) url.getContent();
content = IOUtils.toString(s, "UTF-8");
} finally {
if (s != null) s.close();
}
return content.toString();
}
return null;
}
}
System.setProperty("javax.net.debug", "all");
异常
javax.net.ssl.SSLException: Received fatal alert: protocol_version
如果因任何原因握手失败,SSLSocket将关闭,无法进行进一步的通信。
以上示例的Observer LOG示例:
*** ClientHello, TLSv1.2
RandomCookie: GMT: 1505482843 bytes = { 12, 11, 111, 99, 8, 177, 101, 27, 84, 176, 147, 215, 116, 208, 31, 178, 141, 170, 29, 118, 29, 192, 61, 191, 53, 201, 127, 100 }
Session ID: {}
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_ECDSA_WITH_RC4_128_SHA, TLS_ECDHE_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_SHA, TLS_ECDH_ECDSA_WITH_RC4_128_SHA, TLS_ECDH_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_MD5, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
Extension elliptic_curves, curve names: {secp256r1, sect163k1, sect163r2, secp192r1, secp224r1, sect233k1, sect233r1, sect283k1, sect283r1, secp384r1, sect409k1, sect409r1, secp521r1, sect571k1, sect571r1, secp160k1, secp160r1, secp160r2, sect163r1, secp192k1, sect193r1, sect193r2, secp224k1, sect239k1, secp256k1}
Extension ec_point_formats, formats: [uncompressed]
Extension signature_algorithms, signature_algorithms: SHA512withECDSA, SHA512withRSA, SHA384withECDSA, SHA384withRSA, SHA256withECDSA, SHA256withRSA, SHA224withECDSA, SHA224withRSA, SHA1withECDSA, SHA1withRSA, SHA1withDSA, MD5withRSA
Extension server_name, server_name: [host_name: raw.githubusercontent.com]
***
[write] MD5 and SHA1 hashes: len = 213
0000: 01 00 00 D1 03 03 5A BC D8 5B 0C 0B 6F 63 08 B1 ......Z..[..oc..
0010: 65 1B 54 B0 93 D7 74 D0 1F B2 8D AA 1D 76 1D C0 e.T...t......v..
0020: 3D BF 35 C9 7F 64 00 00 2A C0 09 C0 13 00 2F C0 =.5..d..*...../.
0030: 04 C0 0E 00 33 00 32 C0 08 C0 12 00 0A C0 03 C0 ....3.2.........
0040: 0D 00 16 00 13 C0 07 C0 11 00 05 C0 02 C0 0C 00 ................
0050: 04 00 FF 01 00 00 7E 00 0A 00 34 00 32 00 17 00 ..........4.2...
0060: 01 00 03 00 13 00 15 00 06 00 07 00 09 00 0A 00 ................
0070: 18 00 0B 00 0C 00 19 00 0D 00 0E 00 0F 00 10 00 ................
0080: 11 00 02 00 12 00 04 00 05 00 14 00 08 00 16 00 ................
0090: 0B 00 02 01 00 00 0D 00 1A 00 18 06 03 06 01 05 ................
00A0: 03 05 01 04 03 04 01 03 03 03 01 02 03 02 01 02 ................
00B0: 02 01 01 00 00 00 1E 00 1C 00 00 19 72 61 77 2E ............raw.
00C0: 67 69 74 68 75 62 75 73 65 72 63 6F 6E 74 65 6E githubuserconten
00D0: 74 2E 63 6F 6D t.com
main, WRITE: TLSv1.2 Handshake, length = 213
[Raw write]: length = 218
0000: 16 03 03 00 D5 01 00 00 D1 03 03 5A BC D8 5B 0C ...........Z..[.
0010: 0B 6F 63 08 B1 65 1B 54 B0 93 D7 74 D0 1F B2 8D .oc..e.T...t....
0020: AA 1D 76 1D C0 3D BF 35 C9 7F 64 00 00 2A C0 09 ..v..=.5..d..*..
0030: C0 13 00 2F C0 04 C0 0E 00 33 00 32 C0 08 C0 12 .../.....3.2....
0040: 00 0A C0 03 C0 0D 00 16 00 13 C0 07 C0 11 00 05 ................
0050: C0 02 C0 0C 00 04 00 FF 01 00 00 7E 00 0A 00 34 ...............4
0060: 00 32 00 17 00 01 00 03 00 13 00 15 00 06 00 07 .2..............
0070: 00 09 00 0A 00 18 00 0B 00 0C 00 19 00 0D 00 0E ................
0080: 00 0F 00 10 00 11 00 02 00 12 00 04 00 05 00 14 ................
0090: 00 08 00 16 00 0B 00 02 01 00 00 0D 00 1A 00 18 ................
00A0: 06 03 06 01 05 03 05 01 04 03 04 01 03 03 03 01 ................
00B0: 02 03 02 01 02 02 01 01 00 00 00 1E 00 1C 00 00 ................
00C0: 19 72 61 77 2E 67 69 74 68 75 62 75 73 65 72 63 .raw.githubuserc
00D0: 6F 6E 74 65 6E 74 2E 63 6F 6D ontent.com
[Raw read]: length = 5
0000: 16 03 03 00 5D ....]
使用whatsapp进行加密和安全通信

@see
答案 5 :(得分:2)
我得到了同样的错误。 对于Java版本7,以下版本适用于我。
java.lang.System.setProperty(“https.protocols”,“TLSv1.2”);
答案 6 :(得分:1)
这是因为您发送了TLSv1握手,但随后您使用SSLv2协议发送消息;
xxx, WRITE: TLSv1 Handshake, length = 75
xxx, WRITE: SSLv2 client hello message, length = 101
这意味着服务器需要使用TLSv1协议,并且不接受连接。尝试指定要使用的协议,或发布一些相关代码,以便我们看看
答案 7 :(得分:1)
您可以尝试在上一次输入JAVA_OPTS之后在catalina.bat中添加以下行
set JAVA_OPTS =%JAVA_OPTS%-Dhttps.protocols = TLSv1.2 -Djdk.tls.client.protocols = TLSv1.2
答案 8 :(得分:1)
更新到JDK 1.8后出现了该错误。但是JAVA_HOME变量还被硬编码为JDK 1.7。的修改解决了这个问题:
set JAVA_HOME=C:\Program Files\Java\jdk1.8.0_241
答案 9 :(得分:0)
不确定是否找到答案,但是我遇到了这个问题,需要将TLS版本升级到1.2
private HttpsURLConnection getSSlConnection(String url, String username, String password){
SSLContext sc = SSLContext.getInstance("TLSv1.2")
// Create a trust manager that accepts all SSL sites
TrustManager[] trustAllCerts = new TrustManager[1]
def tm = new X509TrustManager(){
@Override
public void checkClientTrusted(X509Certificate[] certs, String authType) {
}
@Override
public void checkServerTrusted(X509Certificate[] x509Certificates, String s) throws CertificateException {
}
@Override
X509Certificate[] getAcceptedIssuers() {
return new X509Certificate[0]
}
}
trustAllCerts[0] = tm
sc.init(null, trustAllCerts, new SecureRandom())
HttpsURLConnection connection = (HttpsURLConnection) getConnection(url, username, password)
connection.setSSLSocketFactory(sc.getSocketFactory())
return connection
}
答案 10 :(得分:0)
我正在将apache-tomcat- 7.0.70 与 jdk1.7.0_45 结合使用,而这里和其他关于stackoverflow的解决方案都没有对我有用。只是共享此解决方案,因为它有望对某人有所帮助,因为这在Google搜索中非常重要
这两个步骤都有效:
-
通过将tomcat添加到tomcat / bin / setenv.sh(在Windows上语法稍有不同),以“ export JAVA_OPTS =“ $ JAVA_OPTS -Dhttps.protocols = TLSv1.2”开始我的tomcat。
-
使用TLS1.2协议手动构建/强制HttpClient或您需要执行的其他任何操作:
Context ctx = SSLContexts.custom().useProtocol("TLSv1.2").build(); HttpClient httpClient = HttpClientBuilder.create().setSslcontext(ctx).build(); HttpPost httppost = new HttpPost(scsTokenVerificationUrl); List<NameValuePair> paramsAccessToken = new ArrayList<NameValuePair>(2); paramsAccessToken.add(new BasicNameValuePair("token", token)); paramsAccessToken.add(new BasicNameValuePair("client_id", scsClientId)); paramsAccessToken.add(new BasicNameValuePair("secret", scsClientSecret)); httppost.setEntity(new UrlEncodedFormEntity(paramsAccessToken, "utf-8")); //Execute and get the response. HttpResponse httpResponseAccessToken = httpClientAccessToken.execute(httppost); String responseJsonAccessToken = EntityUtils.toString(httpResponseAccessToken.getEntity());
答案 11 :(得分:0)
对于使用IBM JDK的用户,您需要将此参数提供给JVM。
-Dcom.ibm.jsse2.overrideDefaultTLS=true
我使用的是Liberty,因此在jvm.options文件中进行了设置。
答案 12 :(得分:0)
public class SecureSocket {
static {
// System.setProperty("javax.net.debug", "all");
System.setProperty("https.protocols", "TLSv1,TLSv1.1,TLSv1.2");
}
public static void main(String[] args) {
String GhitHubSSLFile = "https://raw.githubusercontent.com/Yash-777/SeleniumWebDrivers/master/pom.xml";
try {
String str = readCloudFileAsString(GhitHubSSLFile);
// new String(Files.readAllBytes(Paths.get( "D:/Sample.file" )));
System.out.println("Cloud File Data : "+ str);
} catch (IOException e) {
e.printStackTrace();
}
}
public static String readCloudFileAsString( String urlStr ) throws java.io.IOException {
if( urlStr != null && urlStr != "" ) {
java.io.InputStream s = null;
String content = null;
try {
URL url = new URL( urlStr );
s = (java.io.InputStream) url.getContent();
content = IOUtils.toString(s, "UTF-8");
}
}
return content.toString();
}
return null;
}
答案 13 :(得分:0)
就我而言,只有以下解决方案有效
private static CloseableHttpClient buildHttpClient() {
System.setProperty("https.protocols", "TLSv1.2");
SSLContext ctx = null;
try {
ctx = SSLContexts.custom().useProtocol("TLSv1.2").build();
} catch (KeyManagementException e) {
// TODO Auto-generated catch block
e.printStackTrace();
} catch (NoSuchAlgorithmException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
CloseableHttpClient httpClient =
HttpClientBuilder.create().setSslcontext(ctx).build();
return httpClient;
}
答案 14 :(得分:0)
[使用 JBoss]
- 打开配置路径:
JBOSS_HOME/standalone/configuration/standalone.xml 或
JBOSS_HOME/standalone/configuration/standalone-full.xml
在“<system-properties>”标签内,添加以下行:
<property name="https.protocols" value="TLSv1,TLSv1.1,TLSv1.2"/>
它为我解决了问题。
- javax.net.ssl.SSLException:收到致命警报:protocol_version
- javax.net.ssl.SSLException:收到致命警报:bad_record_mac
- javax.net.ssl.SSLException:收到致命警报:internal_error
- 获取javax.net.ssl.SSLException:收到致命警报:使用Jsoup抓取数据时的protocol_version
- javax.net.ssl.SSLException:收到致命警报:使用Selenium
- javax.net.ssl.SSLException:收到致命警报:unexpected_message
- 调用Web服务:javax.net.ssl.SSLException:收到致命警报:protocol_version
- Jmeter 3.1- javax.net.ssl.SSLException:收到致命警报:protocol_version
- 为什么我得到javax.net.ssl.SSLException:收到致命警报:ant的protocol_version?
- 引起原因:javax.net.ssl.SSLException:收到致命警报:protocol_version
- 我写了这段代码,但我无法理解我的错误
- 我无法从一个代码实例的列表中删除 None 值,但我可以在另一个实例中。为什么它适用于一个细分市场而不适用于另一个细分市场?
- 是否有可能使 loadstring 不可能等于打印?卢阿
- java中的random.expovariate()
- Appscript 通过会议在 Google 日历中发送电子邮件和创建活动
- 为什么我的 Onclick 箭头功能在 React 中不起作用?
- 在此代码中是否有使用“this”的替代方法?
- 在 SQL Server 和 PostgreSQL 上查询,我如何从第一个表获得第二个表的可视化
- 每千个数字得到
- 更新了城市边界 KML 文件的来源?